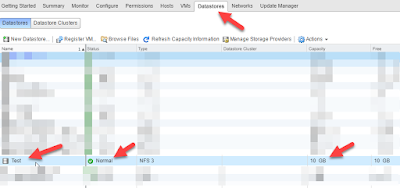
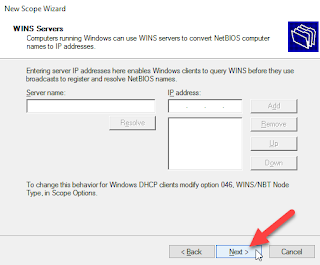
1. First off, you need to map out the following:
a. Your pool of NAT addresses.
b. Your pool of inside addressing going to be going through the NAT.
c. Your interface facing the inside of your network.
d. Your interface facing the outside that is going to the NAT.
2. Once you have the information, you create a scope for your inside network with an Access-List:
a. #access-list 1 permit 10.x.x.x 0.255.255.255
3. Next you need to create your NAT pool (you can do this before or after your access list but it works the same):
a. #ip nat pool TESTPOOL 100.x.x.x 102.x.x.x netmask 255.255.255.0
4. Now, you link your access-list to the NAT pool you just created. This sends your access-list through the NAT pool and will be utilizing the addresses in this pool for the NAT.
a. #ip nat inside source list 1 pool TESTPOOL
5. Finally, you apply NAT to your inside and outside interfaces:
a. #interface TenGigabitEthernet1/0
i. #ip nat inside
b. #interface TenGigabitEthernet2/0
i. #ip nat outside
c. #end
6. You have now assigned a group of IP addresses on your inside network, to a NAT pool facing the outside network. Also, you indicated where the NAT is going on the inside and outside of your interfaces.
References: https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13772-12.html
a. Your pool of NAT addresses.
b. Your pool of inside addressing going to be going through the NAT.
c. Your interface facing the inside of your network.
d. Your interface facing the outside that is going to the NAT.
2. Once you have the information, you create a scope for your inside network with an Access-List:
a. #access-list 1 permit 10.x.x.x 0.255.255.255
3. Next you need to create your NAT pool (you can do this before or after your access list but it works the same):
a. #ip nat pool TESTPOOL 100.x.x.x 102.x.x.x netmask 255.255.255.0
4. Now, you link your access-list to the NAT pool you just created. This sends your access-list through the NAT pool and will be utilizing the addresses in this pool for the NAT.
a. #ip nat inside source list 1 pool TESTPOOL
5. Finally, you apply NAT to your inside and outside interfaces:
a. #interface TenGigabitEthernet1/0
i. #ip nat inside
b. #interface TenGigabitEthernet2/0
i. #ip nat outside
c. #end
6. You have now assigned a group of IP addresses on your inside network, to a NAT pool facing the outside network. Also, you indicated where the NAT is going on the inside and outside of your interfaces.
References: https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13772-12.html